Understand Google cloud storage Encryption options and hands on step-by-step tutorials to encrypt cloud storage using customer managed keys.
In cloud storage data encryption is the process to encode data before it is saved on disk to prevent unauthorized access. It is an important step to prevent tampering of sensitive data.
One of the most important things before storing data or files on cloud is to encrypt it.
Google Cloud Storage always encrypts data at server side before it is saved to disk for free of cost.
Table of Contents
Client-side data encryption
To learn and explore Google Cloud platform for free refer, Google Cloud Free Credits – Google Cloud Tutorials . Free Tier account provides 300 $ worth credit to learn and explore google cloud services over period of 90 days.
In client-side data encryption it is expected that the user must encrypt the data before it is sent to cloud storage. When reading the data from cloud storage user is responsible to decrypt the data.
The second layer of data encryption is server-side encryption. In Server-side data encryption google cloud storage (GCS) is responsible to encrypt the data before it is saved to the storage disk and also decrypt it based on valid key.
Google-managed encryption keys: Server-side encryption
Google managed encryption is the default server-side encryption implemented by GCS and no separate configuration is required.
Whenever a file or data is uploaded to storage bucket, and you don’t specify any configuration related to data encryption Google – Managed encryption is performed.
Keys managed by google are used to encrypt/decrypt your data.
If you are new to Google Cloud Storage buckets and how to configure and manage storage buckets learn more here, Google Cloud Storage Free – Google Cloud Tutorials
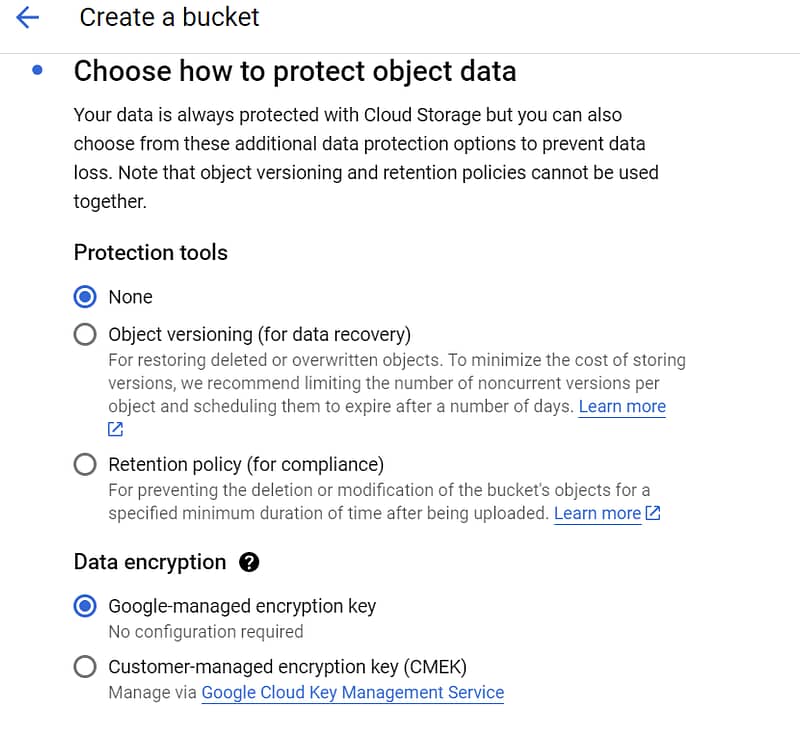
How to Check/Modify Google-managed encryption keys in Cloud Storage bucket
- In google cloud console search for “Storage bucket”
- Once you navigate to storage bucket page click on create new bucket.
- Enter your unique bucket name (check here for bucket name requirements Google Cloud Storage Free – Google Cloud Tutorials)
- Select a valid location type as per your requirements
- Specify default storage class for this bucket
- In data protection tab under Data Encryption by default “Google Managed encryption key” option is checked
- Click on create button
When new files/data is uploaded to this storage bucket google cloud storage manages server-side encryption using Google managed keys.
Customer-managed encryption keys
In some cases when the data sensitivity is very high, and user needs to take complete control of encryption keys customer managed encryption are used.
Customer managed encryption are created and modified in cloud KMS.
When a cloud storage bucket is configured to use Customer managed encryption keys any data uploaded to this bucket will be encrypted and decrypted based on the keys managed by user.
Note: Google Cloud Storage account must have access to KMS to correctly encrypt and decrypt data based on custom keys.
How to Configure Customer-managed encryption keys in Cloud Storage bucket
Enable Cloud Key management service API in your GCP project
Cloud KMS service allows you to create and manage cryptographic keys and perform cryptographic operations.
Key Ring created using KMS service is not provided free of cost and detailed pricing can be found here Pricing | Cloud Key Management Service | Google Cloud.
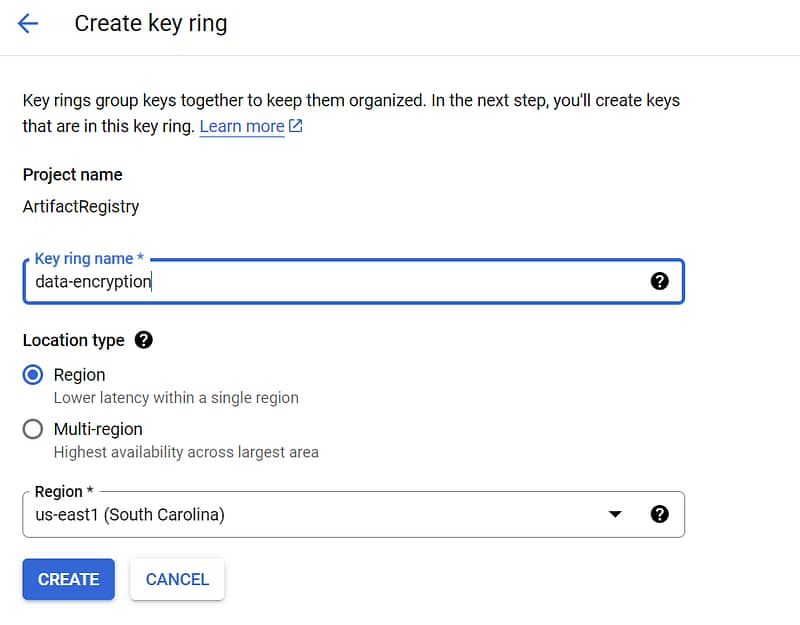
Create new Key Ring
- In Google cloud console search “Key management”
- Click on Create key ring
- Enter key name
- Enter location
- Click on create
Create Keys
- Select key ring
- In key ring click on create new key
- Add key name and protection layer
- select key material as generated
- select purpose as symmetric encrypt/decrypt
- Choose defaults for version and additional settings.

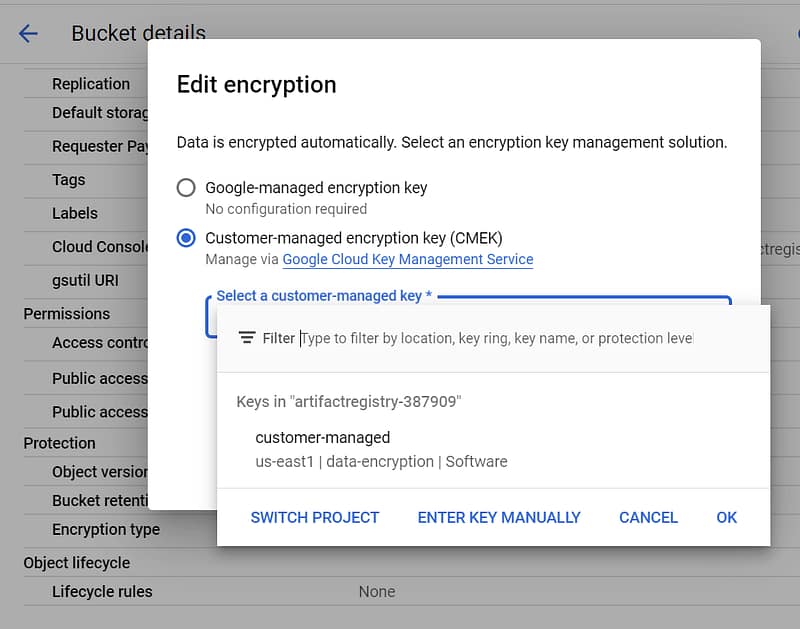
Search for your storage bucket and click on edit configuration.
Assign customer managed key created in key Ring.

Customer-Supplied Keys: Server-side encryption
in rare cases of elevated security google and customer managed keys created using cloud KMS might not suffice the need.
In such cases customer supplied keys can be used to encrypt cloud storage data. Google cloud storage does not store keys.
Customer supplies the key with every GCS operation. Customer is responsible for storing it and using in when making API calls.
The encrypted key along with encryption algorithm data can be passed using API headers when making API calls.
FAQ
Is Google cloud storage encrypted?
Google Cloud Storage always encrypts data at server side before it is saved to disk for free of cost when google managed encryption is selected. It is default option when new storage bucket is created.
How do I encrypt my cloud storage data?
Cloud storage data in GCP can encrypted by user on client side and GCP can encrypt it on server side using google managed keys, customer managed keys or customer supplied keys.